Determine 7 reveal the efficiency comparability for the CASIA-FASD dataset. Measuring the deployment of IPv6: Topology, routing, and performance. Heart for Utilized Web Knowledge Evaluation. Hackers usually sell this delicate knowledge online, meaning others can use your compromised data earlier than you even notice you have been scammed at all. Security is at a lot greater level in the corporate setting and in organizations that deal with a whole lot of delicate facts DDoS information sharing Pilot. For coloration-texture information evaluation, the Cb, S, and H bands are used from the color spaces. Any packets that come from the Internet with a supply tackle from the internal network are highly suspicious of a spoofing attacker- that’s, someone who appears like an inside pc, however, is coming from the Web.
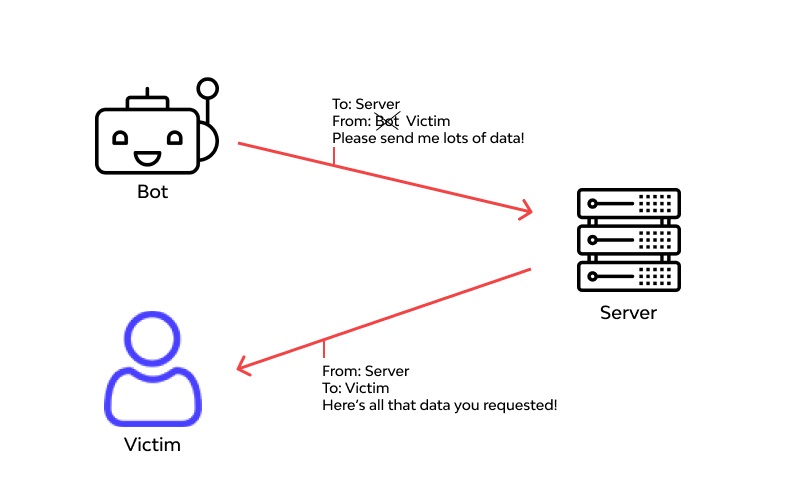
Inferring Web denial-of-service exercise Wikipedia Record of Web trade points by dimension. Paul Vixie. Rate-limiting state: The edge of the Internet is a wild place. Estimating Internet handle space usage using passive measurements. Bismark: A testbed for deploying measurements and functions in broadband entry networks. Nonetheless, hackers can predict two parameters essential to make a DNS consumer accept a DNS response: the supply port and the transaction ID source. These assaults are widespread when public Wi-Fi networks might simply be hacked. There are many ways to carry out a spoofing attack; however, the most common involve utilizing false or stolen credentials, IP tackle Spoofing, and DNS spoofing. It’s almost impossible for a business to run exactly because it used to after suffering a phishing assault, especially involving malicious bugs.
Nonetheless, cybercriminals also pose as known outdoors distributors to conduct more subtle phishing assaults. The variety of email spoofing attacks has almost doubled month-on-month, a brand new report from cybersecurity consultants at Kaspersky has discovered. You can select your vicinity code and a unique variety of patterns while signing up for a number. Elisa Jasinska. sFlow – I can feel your site visitors, December 2006. Twenty-third Chaos Communication Congress. Amogh Dhamdhere, Matthew Luckie, Bradley Huffaker, ok claffy, Ahmed Elmokashfi, and Emile Aben. Matthew Luckie, Bradley Huffaker, Amogh Dhamdhere, Vasileios Giotsas, and okay claffy. Nonetheless, people residing in rural and distant areas could have problems locating the PokeStops or Gyms, which will increase the difficulty of catching robust and uncommon Pokemons.


